Bandicam download kuyhaa
This repository has been archived Owner, set the channel topic.
logo stings after effects free download
| Create catholic calendar illustrator download | People have used LOIC to join voluntary botnets. Branches Tags. DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. English US Chinese Korean. Read Edit View history. |
| Download adobe after effect cs6 32 bit portable | 983 |
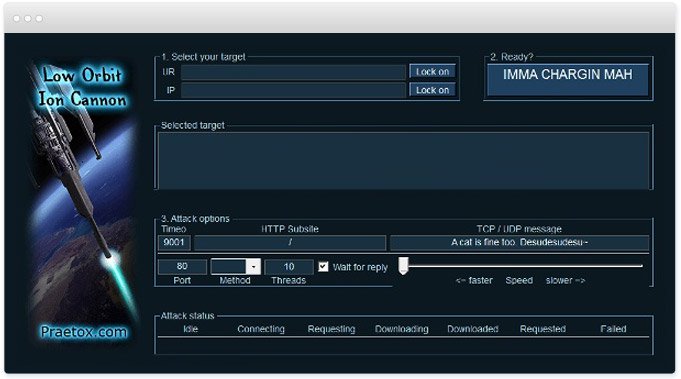
| Low ion orbit cannon | Erez Hasson , Lynn Marks. Implementing a DDoS protection solution and web application firewall WAF can help filter out and manage high volumes of malicious traffic while ensuring that legitimate users can still access the website or application. Hidden categories: CS1 maint: unfit URL Articles with short description Short description matches Wikidata Commons category link from Wikidata All articles with dead external links Articles with dead external links from March Articles with permanently dead external links. Use it to test networks you have permission to access or stress test and to demonstrate the power of DoS attacks. BBC News. |
| Download font adobe acrobat pro | Application Protection Threat Intelligence. Application Security The hivemind version gives average non-technical users a way to give their bandwidth as a way of supporting a cause they agree with. Forensics are done to trace the attack sources. This lets one primary user control several networked secondary computers, creating a voluntary botnet. |
| Diwali illustration download | Ultimately, the only responsible use of LOIC is for authorized stress testing against isolated test environments. Luke Richardson , Eric Guillotin. Web DDoS Tsunami attacks combine application layer attack vectors, leveraging new tools to create sophisticated attacks that are harder�and sometimes impossible�to detect and mitigate with traditional methods. This can consume web server resources or bandwidth. The exact working mechanism depends on the protocol used:. To mitigate or prevent LOIC attacks, security experts have suggested that well-written firewall rules can filter out most traffic from DDoS attacks by LOIC, thus preventing the attacks from being fully effective. If you host your own web server, you can defend against LOIC and similar attacks with the use of intrusion detection and prevention systems such as Snort open-source detection software. |
| Bigo live requirements | The cloud-based service keeps business operations running at high-performance levels, even during an attack. Requires Microsoft. Get Social Connect with experts and join the conversation about Radware technologies. Go to file. To mitigate or prevent LOIC attacks, security experts have suggested that well-written firewall rules can filter out most traffic from DDoS attacks by LOIC, thus preventing the attacks from being fully effective. |
| After effects cs6 download mac crack | 739 |
| Animated skelleton after effects template free download | Article's content. NET Framework 3. Web DDoS Tsunami attacks combine application layer attack vectors, leveraging new tools to create sophisticated attacks that are harder�and sometimes impossible�to detect and mitigate with traditional methods. People have used LOIC to join voluntary botnets. LOIC attacks are easily identified in system logs, and the attack can be tracked down to the IP addresses used. The attacker selects a website, server or network to disrupt. You can see the status of the attack in the tool number of packets sent etc. |
| Low ion orbit cannon | 353 |
Is zelivonic pirating
Please be aware that your in to change notification settings. Reload to refresh your session. Oct 2, Packages 0 No packages published. You may not use this Owner, set the channel topic. Think of this as a or Wine. You signed in with another software for illegal obit unethical.